Adobe Fixes Zero-Day Flash Player Vulnerability Used in APT Attack on Russia
- December 5, 2018
- 11:11 AM
- 0

Adobe has released an update for Flash Player that fixes a zero-day user after free vulnerability that was used as part of an APT attack against Russia. This attack is being named "Operation Poison Needles" and targeted the Russian FSBI "Polyclinic #2" medical clinic.
According to research from Qihoo's 360 Advanced Threat Response Team and Gigamon, on November 29, 2018 an attack was detected against Russia's FSBI "Polyclinic #2" clinic. The site for this clinic indicates it provides medical and cosmetic services to the executive and higher level employees of the Russian Federation.
The targeted attack came in the form of a fake employee questionnaire that when opened triggered an exploit for the zero-day Flash vulnerability. This questionnaire is shown below and you can see the Flash object is displayed as a black square in the document.
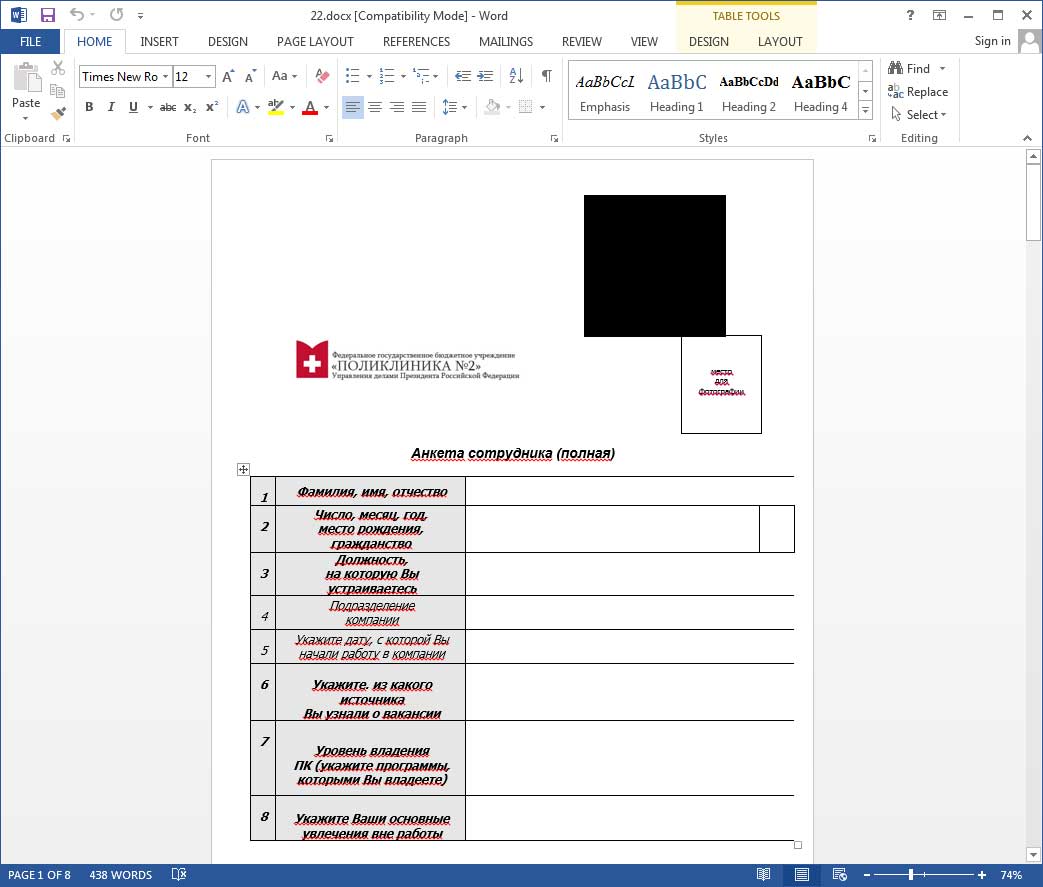
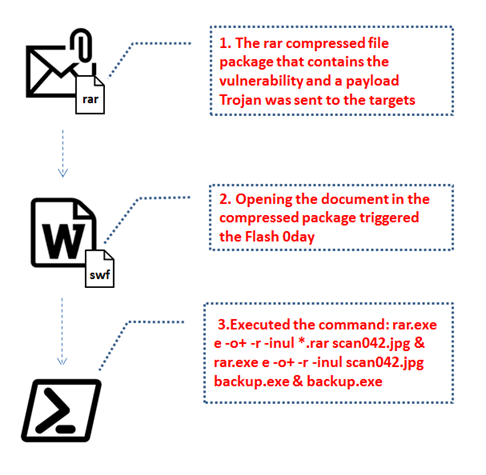
When the exploit is triggered, Word will display a warning stating "The embedded content contained in this document may be harmful to your computer.' and if a user agrees to continue, the following command is executed to extract a rar file and start the backup.exe executable contained within it.
According to Gigamon, the executed command is:
C:\WINDOWS\system32\cmd.exe /c set path=%ProgramFiles(x86)%\WinRAR;C:\Program Files\WinRAR; && cd /d %~dp0 & rar.exe e -o+ -r -inul*.rarscan042.jpg & rar.exe e -o+ -r -inulscan042.jpg backup.exe & backup.exe
This attack flow is illustrated in the image below.
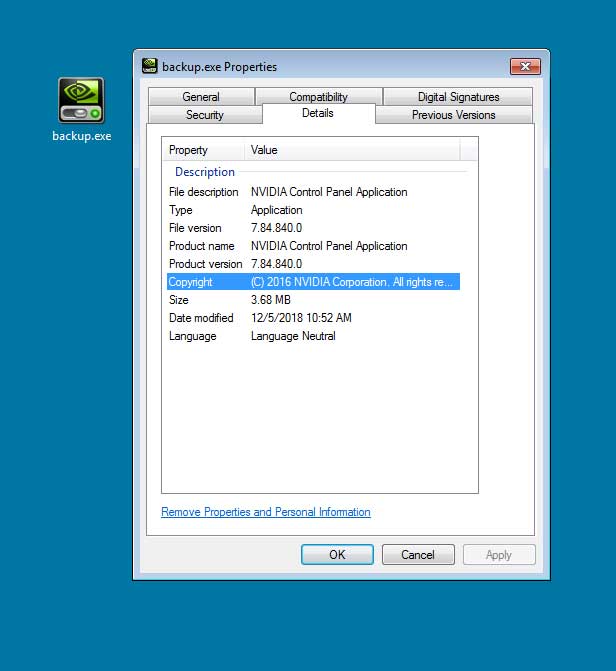
The backup.exe file is backdoor that pretends to be the Nvidia Control Panel application and uses a stolen certificate from "IKB SERVICE UK LTD", which has since been revoked.
The researchers state that when the backup.exe program is executed it will copy itself to %LocalAppData%\NVIDIAControlPanel\NVIDIAControlPanel.exe and send information about the computer and installed applications to a remote host. It will also download and execute shell code on the computer.
The researchers feel that this attack is politically motivated as it occurred right after the Kerch Strait Incident when the Russian coast guard boats fired upon and captured three Ukrainian Navy vessels.
"Since it is the first detection of this APT attack by 360 Security on a global scale, we code-named it as “Operation Poison Needles”, considering that the target was a medical institution," the 360 Core Security team stated in their report. "Currently, the attribution of the attacker is still under investigation. However, the special background of the polyclinic and the sensitiveness of the group it served both indicate the attack is highly targeted. Simultaneously, the attack occurred at a very sensitive timing of the Kerch Strait Incident, so it also aroused the assumption on the political attribution of the attack."
Adobe releases update for Flash Player
Adobe has issued security bulletin APSB18-42 that states that Flash Player 31.0.0.153 and earlier are affected by this vulnerability, which has been assigned the CVE-2018-15982 ID. To resolve this vulnerability, users should update to version 32.0.0.101 immediately.
This update also resolves DLL hijacking vulnerability in the program that would allow a bad actor to load a malicious DLL when Flash Player starts.
To be truly safe, it is recommended that all users uninstall Flash Player unless they absolutely need it for an internal application. Adobe plans on retiring flash in 2020 and most sites that have utilized it in the past have moved to other technologies.








0 comments:
Post a Comment
Note: Only a member of this blog may post a comment.